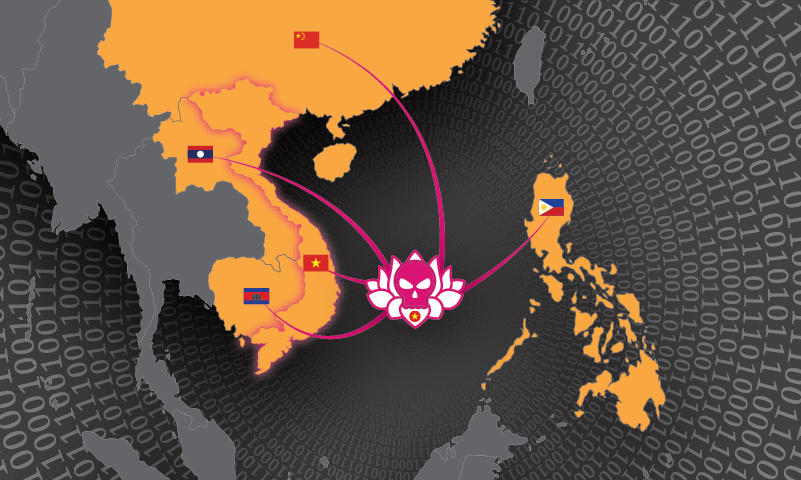
In May 2017, Volexity identified and started tracking a very sophisticated and extremely widespread mass digital surveillance and attack campaign targeting several Asian nations, the ASEAN organization, and hundreds of individuals and organizations tied to media, human rights and civil society causes. These attacks are being conducted through numerous strategically compromised websites and have occurred over several high-profile ASEAN summits. Volexity has tied this attack campaign to an advanced persistent threat (APT) group first identified as OceanLotus by SkyEye Labs in 2015. OceanLotus, also known as APT32, is believed to be a Vietnam-based APT group that has become increasingly sophisticated in its attack tactics, techniques, and procedures (TTPs). Volexity works closely with several human rights and civil society organizations. A few of these organizations have specifically been targeted by OceanLotus since early 2015. As a result, Volexity has been able to directly observe and investigate various attack campaigns. This report is based on a very targeted attack that Volexity observed and the research that followed.
Key highlights of this most recent and ongoing attack campaign by the OceanLotus group are as follows:
- Massive digital profiling and information collection campaign via strategically compromised websites
- Over 100 websites of individuals and organizations tied to Government, Military, Human Rights, Civil Society, Media, State Oil Exploration, and more used to launch attacks around the globe
- Use of whitelists to target only specific individuals and organizations
- Custom Google Apps designed for gaining access to victim Gmail accounts to steal e-mail and contacts
- Strategic and targeted JavaScript delivery to modify the view of compromised websites to facilitate social engineering of visitors to install malware or provide access to e-mail accounts
- Large distributed attack infrastructure spanning numerous hosting providers and countries
- Numerous attacker created domains designed to mimic legitimate online services and organizations such as AddThis, Disqus, Akamai, Baidu, Cloudflare, Facebook, Google, and others
- Heavy uses of Let’s Encrypt SSL/TLS certificates
- Use of multiple backdoors, such as Cobalt Strike and others, believed to be developed and solely used by OceanLotus
Volexity believes the size and scale of this attack campaign have only previously been rivaled by a Russian APT group commonly referred to as Turla and documented in a report from Symantec called The Waterbug attack group. The OceanLotus threat group has successfully operated, largely unnoticed, through several high-profile websites since late 2016. Volexity has observed the following operating pattern for the OceanLotus group:
- Compromise website of strategic importance (e.g. websites visitors have a higher likelihood to be targets of interest)
- Add one or more webshell backdoors to victim websites to maintain persistence
- Webshell used to add JavaScript developed by OceanLotus into the website
- The malicious JavaScript makes calls over HTTP or HTTPS to attacker controlled domains to typically load one of two different OceanLotus frameworks
- OceanLotus JavaScript frameworks designed to track, profile, and target the compromised website’s visitors
- Website visitors of interest are flagged for targeting and receive special JavaScript aimed at compromising the user’s system or e-mail accounts
Volexity has also noted that some of the organizations with compromised websites have also been targeted with spear phishing campaigns that attempt to install backdoors on the target systems. Spear phishing activity and detailed malware infrastructure will be described in a follow on report on OceanLotus activity.
Compromised Sites
Volexity has been able to identify a staggeringly large number of websites that have been strategically compromised by the OceanLotus attackers. The number of compromised websites exceeds 100. The overwhelming majority of the websites that have been compromised belong to Vietnamese individuals and organizations that are critical of the Vietnamese Government. The remainder of the compromised websites are tied to one of three countries that share a land border with Vietnam or the Philippines. Unlike with the Vietnamese victims, in most cases these websites are tied to state owned or affiliated organizations.
Vietnam
Volexity has chosen not to list the Vietnamese websites that have been compromised, as the quantity is exceedingly large (over 80) and many of them are tied to individuals or very small organizations. However, the list below characterizes the types of websites that have been victimized to facilitate this ongoing campaign.
- Human Rights
- Civil Society
- News/Media (English and Vietnamese Language)
- Individual Bloggers
- Religion
Height Insoles: Hi, I do believe this is an excellent site. I stumbledupon …
http://fishinglovers.net: Appreciate you sharing, great post.Thanks Again. Keep writi…
Achilles Pain causes: Every weekend i used to pay a quick visit this site, as i w…






December 13, 2017
OceanLotus Blossoms: Mass Digital Surveillance and Attacks Targeting ASEAN, Asian Nations, the Media, Human Rights Groups, and Civil Society
by Nhan Quyen • [Human Rights]
In May 2017, Volexity identified and started tracking a very sophisticated and extremely widespread mass digital surveillance and attack campaign targeting several Asian nations, the ASEAN organization, and hundreds of individuals and organizations tied to media, human rights and civil society causes. These attacks are being conducted through numerous strategically compromised websites and have occurred over several high-profile ASEAN summits. Volexity has tied this attack campaign to an advanced persistent threat (APT) group first identified as OceanLotus by SkyEye Labs in 2015. OceanLotus, also known as APT32, is believed to be a Vietnam-based APT group that has become increasingly sophisticated in its attack tactics, techniques, and procedures (TTPs). Volexity works closely with several human rights and civil society organizations. A few of these organizations have specifically been targeted by OceanLotus since early 2015. As a result, Volexity has been able to directly observe and investigate various attack campaigns. This report is based on a very targeted attack that Volexity observed and the research that followed.
Key highlights of this most recent and ongoing attack campaign by the OceanLotus group are as follows:
Volexity believes the size and scale of this attack campaign have only previously been rivaled by a Russian APT group commonly referred to as Turla and documented in a report from Symantec called The Waterbug attack group. The OceanLotus threat group has successfully operated, largely unnoticed, through several high-profile websites since late 2016. Volexity has observed the following operating pattern for the OceanLotus group:
Volexity has also noted that some of the organizations with compromised websites have also been targeted with spear phishing campaigns that attempt to install backdoors on the target systems. Spear phishing activity and detailed malware infrastructure will be described in a follow on report on OceanLotus activity.
Compromised Sites
Volexity has been able to identify a staggeringly large number of websites that have been strategically compromised by the OceanLotus attackers. The number of compromised websites exceeds 100. The overwhelming majority of the websites that have been compromised belong to Vietnamese individuals and organizations that are critical of the Vietnamese Government. The remainder of the compromised websites are tied to one of three countries that share a land border with Vietnam or the Philippines. Unlike with the Vietnamese victims, in most cases these websites are tied to state owned or affiliated organizations.
Vietnam
Volexity has chosen not to list the Vietnamese websites that have been compromised, as the quantity is exceedingly large (over 80) and many of them are tied to individuals or very small organizations. However, the list below characterizes the types of websites that have been victimized to facilitate this ongoing campaign.